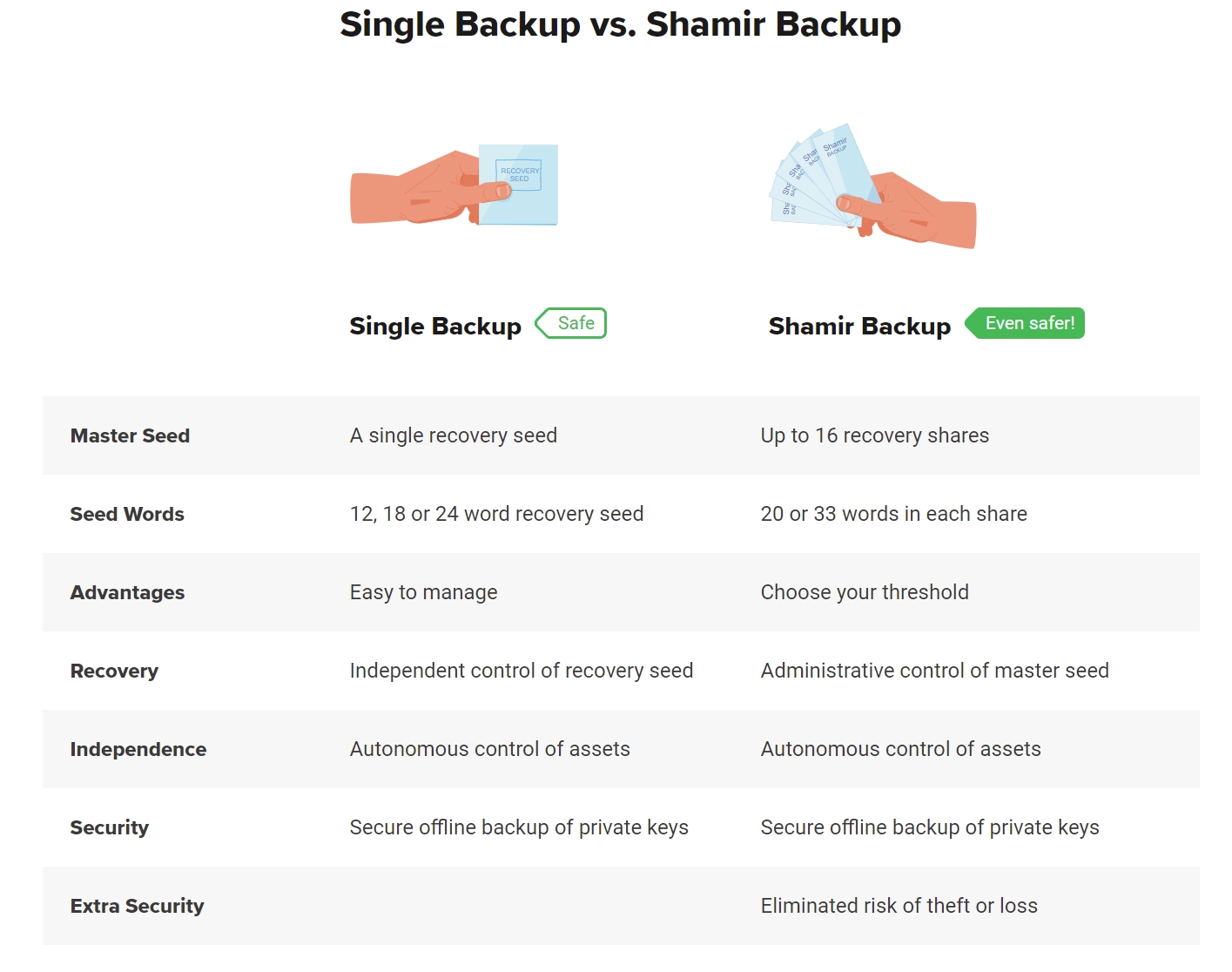
A Shamir backup is a method of securely storing and sharing sensitive information. It is named after its creator, Adi Shamir, one of the founding fathers of modern cryptography. The main idea behind a Shamir backup is to divide a secret into multiple parts, called shares, in such a way that a specified number of shares are required to reconstruct the original secret.
The beauty of a Shamir backup is that any combination of the specified number of shares can be used to reconstruct the secret. This means that the secret can be divided among multiple individuals or stored in different locations, reducing the risk of a single point of failure.
To securely share a Shamir backup, an algorithm is used to split the secret into shares. These shares can then be distributed to different individuals or stored in separate offline locations. To reconstruct the secret, a person needs to collect the required number of shares and use specific software to run the reconstruction algorithm.
One advantage of using a Shamir backup is that even if some of the shares are lost, stolen, or compromised, the original secret can still be reconstructed as long as the specified number of shares is available. This makes it a reliable and secure method for protecting sensitive information.
In conclusion, a Shamir backup is a secure and flexible way to store and share sensitive information. By dividing the secret into shares, the risk of a single point of failure is minimized, and the original secret can be reconstructed even if some shares are lost or compromised. If you are looking for a reliable and secure way to protect your valuable data, a Shamir backup is definitely worth considering.
- Understanding Shamir backup
- What is Shamir backup?
- How does Shamir backup work?
- Benefits of using Shamir backup
- Enhanced security
- Flexibility in backup recovery
- Decreased risk of data loss
- Use cases for Shamir backup
- Securing cryptocurrency wallets
- Safeguarding sensitive business data
- Protecting personal files and documents
- Implementing Shamir Backup
- Choosing the right Shamir backup service
- Setting up Shamir backup for different devices
- Frequently Asked Questions:
- What is a Shamir backup?
- How does a Shamir backup work?
- Why is Shamir backup important?
- Can I use a Shamir backup for my cryptocurrency wallet?
- Video:
- How to use Shamir Backup with Trezor Model T
- How to Securely Store Your Seed Phrase: 2/3 split or SSS (Shamir Secret Sharing)
Understanding Shamir backup

Shamir backup is a method of securely sharing and storing sensitive information by splitting it into multiple shares. This technique is based on the cryptographic concept called secret sharing.
In a Shamir backup, the original data is divided into a certain number of shares, where each share consists of a specified number of characters. These shares are then distributed among different individuals or stored in different locations.
One of the main reasons why Shamir backup is considered secure is that a minimum number of shares is required to reconstruct the original data. For example, if a backup is divided into five shares, only three of those shares may be needed to reconstruct the data. This adds an extra layer of security, as even if one or two shares are compromised, the original data remains safe.
The shares generated through Shamir backup can be stored both online and offline, depending on the requirements and preferences of the user. While some individuals may choose to keep their shares stored securely on their devices or in the cloud, others may opt for an offline approach, such as printing the shares and keeping them in physical form.
To reconstruct the original data from the shares, specialized software or algorithms are required. These software or algorithms use the shares to reconstruct the data without revealing the original information. This ensures that the reconstructed data remains secure.
One important aspect of Shamir backup is that the shares can be securely shared among different individuals. This means that even if multiple people possess different shares, they cannot reconstruct the original data without the required minimum threshold of shares. This feature makes it possible to distribute shares among trusted parties without the risk of unauthorized access.
In summary, Shamir backup is a secure method of dividing sensitive data into shares and storing them in different locations. By requiring a minimum number of shares to reconstruct the data, it adds an extra layer of security. Whether stored online or offline, the shares can be securely shared among trusted parties, and the original data can be reconstructed using specialized software or algorithms.
What is Shamir backup?

Shamir backup, also known as Shamir’s Secret Sharing, is a cryptographic technique used to securely distribute and store sensitive data, such as passwords or encryption keys. It was developed by Adi Shamir, one of the creators of the RSA encryption algorithm.
In a Shamir backup scheme, a secret is divided into multiple parts called shares. The number of shares and the number of shares required to reconstruct the secret are specified by the user. For example, a secret can be divided into five shares, with three shares required to reconstruct the secret.
Each share is independent and does not reveal any information about the original secret. This means that even if some shares are compromised, the secret remains secure as long as the number of compromised shares is below the threshold required for reconstruction.
The shares can be stored securely in different locations, such as on separate devices or with different trusted individuals. This provides an extra layer of security as an attacker would need to gain access to multiple shares to reconstruct the secret.
To reconstruct the secret, a specified number of shares are required. This can be done using specialized software or by manually combining the shares. The reconstructed secret will be identical to the original secret, allowing the user to access their encrypted data or restore their system.
It is important to note that Shamir backups are typically stored offline to further enhance security. By keeping the shares offline, they are less vulnerable to hacking or unauthorized access. This also reduces the risk of losing the shares due to hardware failures or other technical issues.
How does Shamir backup work?
Shamir backup is a method of securely storing data by dividing it into multiple parts called shares. These shares are generated using a special algorithm called Shamir’s Secret Sharing algorithm.
The data is first converted into a series of characters, and then these characters are divided into a specified number of shares. Each share contains a portion of the data, and these shares are stored offline, either physically or digitally, in different locations.
To recover the data, a user needs to collect a certain number of shares, which is specified when the shares are created. This is done by sharing the shares with multiple trusted individuals or storing them in secure locations.
The Shamir’s Secret Sharing algorithm ensures that the original data can be securely reconstructed by combining the shares. This means that even if some shares are lost or compromised, the data can still be recovered.
Shamir backup can be implemented using specialized software or programs designed specifically for this purpose. These software ensure the security and integrity of the shares, making sure they are stored in a secure manner.
Benefits of using Shamir backup
Shamir backup, also known as Shamir’s Secret Sharing, offers several benefits for securely storing and sharing sensitive information:
- Protection against data loss: With Shamir backup, data is divided into multiple shares, ensuring that even if one or more shares are lost or corrupted, the original data can be reconstructed using the remaining shares.
- Flexible sharing options: Shamir backup allows for the creation of multiple shares, with a specified threshold required to reconstruct the original data. This threshold can be set according to the desired level of security and ease of sharing.
- Enhanced security: The use of cryptography in Shamir backup ensures that the shares are securely stored and cannot be easily compromised. This provides an additional layer of protection for sensitive information.
- Offline storage: Shamir backup operates offline, meaning that the shares can be securely stored on physical media such as USB drives or printed paper. This eliminates the risk of online attacks or data breaches.
- Effective sharing: The shares generated by Shamir backup can be easily shared with trusted individuals or stored in different physical locations. This allows for secure collaboration and ensures that access to the original data is not dependent on a single individual or location.
- User-friendly software: There are various software implementations of Shamir backup that provide a user-friendly interface and make it easy to generate and manage shares. This makes it accessible to a wide range of users, even those without technical expertise.
Enhanced security

The Shamir backup is a software that allows users to store sensitive data securely. One of the main features of the Shamir backup is its enhanced security measures.
Unlike traditional backups that are stored in a single location, the Shamir backup splits the data into multiple shares. These shares are then securely distributed to different locations, ensuring that no single point of failure exists. This means that even if one share is compromised, the data is still secure.
The Shamir backup utilizes a cryptographic algorithm to divide the data into shares. These shares can be stored offline on different devices or even on physical mediums like paper or USB drives. This ensures that the data is protected from online threats such as hackers or malware.
When sharing the Shamir backup, the user can specify the number of shares required to reconstruct the data. For example, if the data is split into five shares, the user can specify that at least three shares are required to reconstruct the original data. This provides an additional layer of security, as the data cannot be accessed with just one share.
Furthermore, each share only contains a portion of the original data. This means that even if someone gains access to one share, they will only have a fraction of the data. The remaining shares are required to reconstruct the full data, making it extremely difficult for an attacker to retrieve the complete information.
In conclusion, the Shamir backup provides enhanced security for storing and sharing sensitive data. By splitting the data into multiple shares and encrypting them using a cryptographic algorithm, the Shamir backup ensures that the data is stored securely and protected from unauthorized access.
Flexibility in backup recovery
The Shamir backup is a method of securely storing important data and splitting it into multiple shares. This flexibility in backup recovery allows for a more secure and efficient way of accessing and recovering data.
With Shamir backup, the data is divided into multiple shares, each of which contains a specified number of characters. These shares can then be securely distributed among different individuals or stored in different locations.
One of the main advantages of Shamir backup is the flexibility it offers in terms of sharing and recovery. Since the data is split into multiple shares, any specified number of shares can be used to reconstruct the original data. This means that even if some of the shares are lost or compromised, the data can still be securely reconstructed using the remaining shares.
Additionally, the shares can be stored offline, further enhancing the security of the backup. By keeping the shares in separate physical locations or on separate devices, the risk of losing all the data in case of a single failure or breach is significantly reduced.
Furthermore, the flexibility of Shamir backup allows for easier sharing and collaboration. Multiple individuals or organizations can each hold a different share of the backup, ensuring that no single entity has complete access to the data. This enhances the security of the backup by minimizing the risk of unauthorized access.
In conclusion, the flexibility provided by Shamir backup offers a secure and efficient method of storing and recovering important data. By splitting the data into multiple shares and allowing for secure distribution and reconstruction, the Shamir backup ensures the security and availability of critical information.
Decreased risk of data loss
The Shamir backup method offers a unique and effective way to decrease the risk of data loss. By securing your data through the use of shares, the Shamir backup provides a reliable solution for safeguarding your valuable information.
When using Shamir backup, your data is divided into multiple shares, each containing a subset of the original data. These shares are created using mathematical algorithms, ensuring that each share is unique and contains no duplicate information. This process adds an extra layer of security to your data, as even if one share is compromised, the remaining shares remain secure.
The sharing of the data occurs through the use of Shamir backup software, which allows you to define the number of shares you want to create. This flexibility allows you to customize the level of redundancy you desire, providing a powerful solution for data protection. The shares can be securely stored both online and offline, further reducing the risk of data loss.
In order to restore your data, a specified number of shares are required. For example, if you have created 5 shares, you may set the requirement to restore the data as 3 out of 5 shares. This means that even if a few shares are lost or damaged, you can still restore your data using the remaining valid shares.
The Shamir backup method also offers an added layer of security by allowing you to specify the minimum number of characters required to access the shares. By setting a higher character limit, you can enhance the security of your data and prevent unauthorized access.
In conclusion, the Shamir backup method provides a secure and efficient way to protect your data. By dividing your data into shares and securely storing them, you reduce the risk of data loss and ensure that your information remains confidential. The flexibility and customizable options offered by the Shamir backup method make it an ideal choice for individuals and businesses looking to enhance their data security.
Use cases for Shamir backup
1. Secure storage of sensitive information:
Shamir backup provides a secure way to store sensitive data such as passwords, encryption keys, or private keys. By splitting the data into multiple shares, each stored separately, the risk of unauthorized access is greatly reduced.
2. Sharing important information:
Shamir backup allows for the secure sharing of important information among multiple parties or team members. Instead of relying on a single individual or centralized system, the information can be divided and distributed among several trusted individuals, ensuring that no single person has complete access.
3. Offline storage:
The Shamir backup approach is ideal for offline storage scenarios where the data must be kept secure and accessible even without an internet connection. By splitting the data into shares that can be stored independently, the risk of data loss from hardware failure or cyberattacks is minimized.
4. Reconstruction of lost data:
In cases where important data is lost or corrupted, Shamir backup can provide a reliable method of reconstruction. The shares can be combined using the Shamir’s Secret Sharing algorithm to recreate the original data. This can be particularly useful in disaster recovery scenarios or when restoring encrypted files.
5. Protecting against single points of failure:
By distributing the backup shares among multiple individuals or devices, Shamir backup helps protect against single points of failure. Even if one share is lost or compromised, the original data can still be reconstructed from the remaining shares.
6. Integration with backup software:
Shamir backup can be integrated with backup software to provide an additional layer of security. The software can split the data into shares and distribute them to different storage locations or individuals. This ensures that even if the backup storage is compromised, the data remains secure.
Overall, Shamir backup offers a secure and flexible solution for storing and sharing sensitive information, allowing for offline storage, reconstruction of lost data, and protection against single points of failure.
Securing cryptocurrency wallets
When it comes to storing cryptocurrency, security is of utmost importance. One way to secure cryptocurrency wallets is by using a Shamir backup.
A Shamir backup is a way to securely store the wallet’s private keys by splitting them into multiple parts called “shares.” These shares are typically stored in different physical locations or with different trusted individuals.
The Shamir backup uses a mathematical algorithm called Shamir’s Secret Sharing to divide the private key into several shares. These shares are represented by a set of encoded characters and are securely stored.
To reconstruct the private key and access the wallet, a specified number of shares are required. The original private key can only be reconstructed if the specified number of shares are combined together.
By keeping the shares securely stored in different offline locations or with trusted individuals, the risk of losing the private key or having it stolen is significantly reduced. Even if some shares are lost or compromised, the wallet can still be accessed as long as the specified number of shares are available.
When using a Shamir backup, it is important to use trustworthy software that implements the Shamir’s Secret Sharing algorithm correctly. This ensures that the private key shares are generated and stored securely.
In conclusion, securing cryptocurrency wallets with Shamir backups provides an extra layer of security. By splitting the private key into multiple shares and securely storing them offline or with trusted individuals, the risk of losing or having the key stolen is minimized. As long as the specified number of shares are available, the wallet can be reconstructed and accessed.
Safeguarding sensitive business data

One of the most critical challenges for businesses today is ensuring the security and confidentiality of their sensitive data. With the increasing reliance on digital information, it has become essential to protect important business data from unauthorized access, loss, or theft.
One effective method of safeguarding sensitive business data is through the use of Shamir backup. Shamir backup is a secure method of storing and sharing data that ensures no single entity can access it. Instead, the data is divided into multiple shares, and each share is securely distributed to different individuals or locations.
This sharing of data is done using specialized software that ensures the data is securely transmitted and stored. The software employs advanced encryption techniques to protect the data during transmission and storage, making it virtually impossible for unauthorized parties to access the information.
With Shamir backup, the data shares can be stored in various locations, such as dedicated servers or offline storage devices. This diversification further enhances the security of the data, as even if one location is compromised, the other shares remain secure.
To access the protected data, a defined number of shares must be combined using the Shamir recovery algorithm. The specified number of shares, known as the threshold, determines how many shares are needed to reconstruct the original data. This threshold adds an extra layer of security, as an attacker would need to obtain the required number of shares to gain access to the data.
Shamir backup also allows for the customization of access control. For example, certain shares can be designated only for specific employees or departments, ensuring that only authorized individuals can reconstruct the data. This flexibility makes it possible to enforce strict access controls within an organization.
In addition to its security benefits, Shamir backup offers scalability and convenience. As businesses grow and generate more data, additional shares can be easily created and distributed. This scalable nature allows businesses to adapt to changing data protection needs without compromising security.
In conclusion, Shamir backup provides a secure and reliable method of safeguarding sensitive business data. By dividing the data into shares, distributing them securely, and utilizing advanced encryption techniques, Shamir backup ensures that sensitive data remains protected. With its scalability and customizable access controls, businesses can confidently store and share their valuable information while mitigating the risk of unauthorized access or loss.
Protecting personal files and documents
When it comes to securing personal files and documents, a Shamir backup is a robust solution. With Shamir’s secret sharing algorithm, files can be divided into multiple shares, each containing a portion of the original data. This ensures that even if one share is compromised, the complete file cannot be reconstructed by the unauthorized party.
To protect personal files, specialized software can be used to generate Shamir shares. These shares are created by splitting the original file into multiple parts, which are then encrypted and stored securely. The user specifies the number of shares to generate and the minimum number of shares required to reconstruct the original file.
Each share is represented by a set of characters that can be printed or saved offline. These shares can be distributed to different storage locations or individuals for added security. If the user ever needs to retrieve their file, they can simply collect the specified number of shares and use the software to reconstruct the original data.
Sharing Shamir shares adds an extra layer of security. Rather than relying on a single storage location or relying on a single individual, the shares can be stored in different places or with different people. This way, even if one storage location is compromised or one person becomes untrustworthy, the file remains safe.
It is important to note that keeping the shares offline is crucial for maximum security. By storing the shares offline, the risk of unauthorized access is minimized. The shares can be printed on paper, saved on removable storage devices, or stored in secure physical locations.
| Advantages | Explanation |
|---|---|
| Secure | Shamir shares are encrypted and can be distributed across multiple storage locations or people, minimizing the risk of unauthorized access. |
| Reconstructed | The original file can be reconstructed from the specified number of shares using specialized software. |
| Offline Storage | Shares can be kept offline in physical forms, reducing the chances of unauthorized access. |
In summary, using a Shamir backup provides a secure and reliable method for protecting personal files and documents. By dividing the data into shares, encrypting them, and distributing them offline, the risk of unauthorized access is significantly minimized.
Implementing Shamir Backup

Implementing a Shamir backup involves using special software to generate and manage the shares that will be used to reconstruct the original secret. The software provides a secure and efficient way to generate and store the shares, ensuring the confidentiality and integrity of the original secret.
Here is an overview of the steps involved in implementing a Shamir backup:
- Specify the secret to be protected: The user specifies the secret that they want to protect, such as a private key or a password.
- Generate shares: The software generates a specified number of shares based on the user’s input. Each share is a piece of information that is required to reconstruct the original secret.
- Distribute the shares: The shares are distributed to different storage media or devices, ensuring that each share is stored securely and offline. This prevents a single point of failure and increases the security of the backup.
- Reconstruct the secret: To reconstruct the original secret, a minimum threshold of shares is required. The software uses these shares to mathematically reconstruct the secret. No individual share reveals any information about the secret.
Implementing a Shamir backup provides a secure and reliable way to protect sensitive information. By dividing the secret into multiple shares and distributing them securely, the risk of unauthorized access or data loss is reduced. The software ensures that the shares are generated and stored securely, and offers a convenient way to reconstruct the secret when needed.
In summary, implementing a Shamir backup involves using specialized software to generate shares of a secret, distributing the shares securely to different storage media or devices, and reconstructing the secret using a minimum threshold of shares. This process provides a secure and reliable way to protect sensitive information, ensuring its confidentiality and availability.
Choosing the right Shamir backup service

When it comes to securing your data, choosing the right Shamir backup service is critical. Here are some important factors to consider:
- Specified shares: Ensure that the backup service allows you to specify the number of shares needed to reconstruct the original data. This allows for customizability and flexibility in case of any changes or updates in your data.
- Secure storage: Look for a service that guarantees secure storage for your shares. The Shamir backup service should use advanced encryption techniques to protect your data from unauthorized access.
- Offline sharing: Consider a backup service that allows you to securely share your shares with others offline. This prevents any potential breaches or leaks during online sharing.
- Stored shares: Ensure that the backup service securely stores your shares in multiple locations to avoid the risk of losing all your data in case of a single failure or disaster.
- Reconstruction: Choose a service that provides a reliable and straightforward reconstruction process. It should be able to reconstruct the original data accurately and efficiently.
By considering these factors, you can make an informed decision when choosing the right Shamir backup service. Remember to prioritize the security and confidentiality of your data, as well as the convenience and ease of use provided by the service.
Setting up Shamir backup for different devices

Shamir backup is a secure way to protect your important data and ensure its accessibility in case of hardware failure or loss. It uses a technique called secret sharing to split your data into multiple shares, which can be securely stored in different locations.
To set up a Shamir backup for different devices, follow these steps:
- Install Shamir backup software: Start by installing a Shamir backup software on each device that you want to include in your backup plan. There are several software options available that support Shamir backup, so choose the one that best fits your needs.
- Create a backup: Once the software is installed, open it on each device and follow the instructions to create a backup. This will typically involve selecting the files or folders you want to back up and specifying the desired level of encryption.
- Generate shares: After creating the backup, the software will generate a set of shares. These shares are unique cryptographic keys that are created using the Shamir secret sharing algorithm. The number of shares generated will depend on the settings you choose, but it is recommended to create at least three shares for redundancy.
- Distribute shares: Once the shares are generated, you need to securely distribute them to different locations. This can be done by copying the shares to external storage devices like USB drives, SD cards, or external hard drives. It is important to store these shares offline and in secure locations to prevent unauthorized access.
- Reconstruct the backup: In case you need to restore your data, you can use the Shamir backup software to reconstruct the backup. Simply open the software on any device that has access to at least the specified number of shares and follow the instructions to reconstruct the backup. The software will use the shares to reconstruct the original data.
By setting up Shamir backup for different devices, you can ensure the security and accessibility of your important data even in the event of hardware failure or loss. It provides a reliable and efficient way to protect your data and prevent data loss.
Frequently Asked Questions:
What is a Shamir backup?
A Shamir backup is a method of splitting a crucial piece of information, such as a private key or a password, into multiple parts. These parts, known as shares, are distributed or stored separately for added security.
How does a Shamir backup work?
Shamir backup uses a mathematical algorithm called Shamir’s Secret Sharing scheme. This scheme generates a set of shares from a private key or password. The original information can only be reconstructed when a certain number of these shares are combined.
Why is Shamir backup important?
Shamir backup is important because it enhances the security and resilience of crucial information. By splitting the information into multiple shares, it becomes more difficult for an attacker to gain access to the original data. It also provides a way to recover the information in case one of the shares is lost or compromised.
Can I use a Shamir backup for my cryptocurrency wallet?
Yes, you can use a Shamir backup for your cryptocurrency wallet. Many cryptocurrency wallets and hardware devices support Shamir backup for storing private keys. This adds an extra layer of security and makes it possible to recover access to your wallet even if you lose or damage the original backup.
Video:
How to use Shamir Backup with Trezor Model T
How to Securely Store Your Seed Phrase: 2/3 split or SSS (Shamir Secret Sharing)








