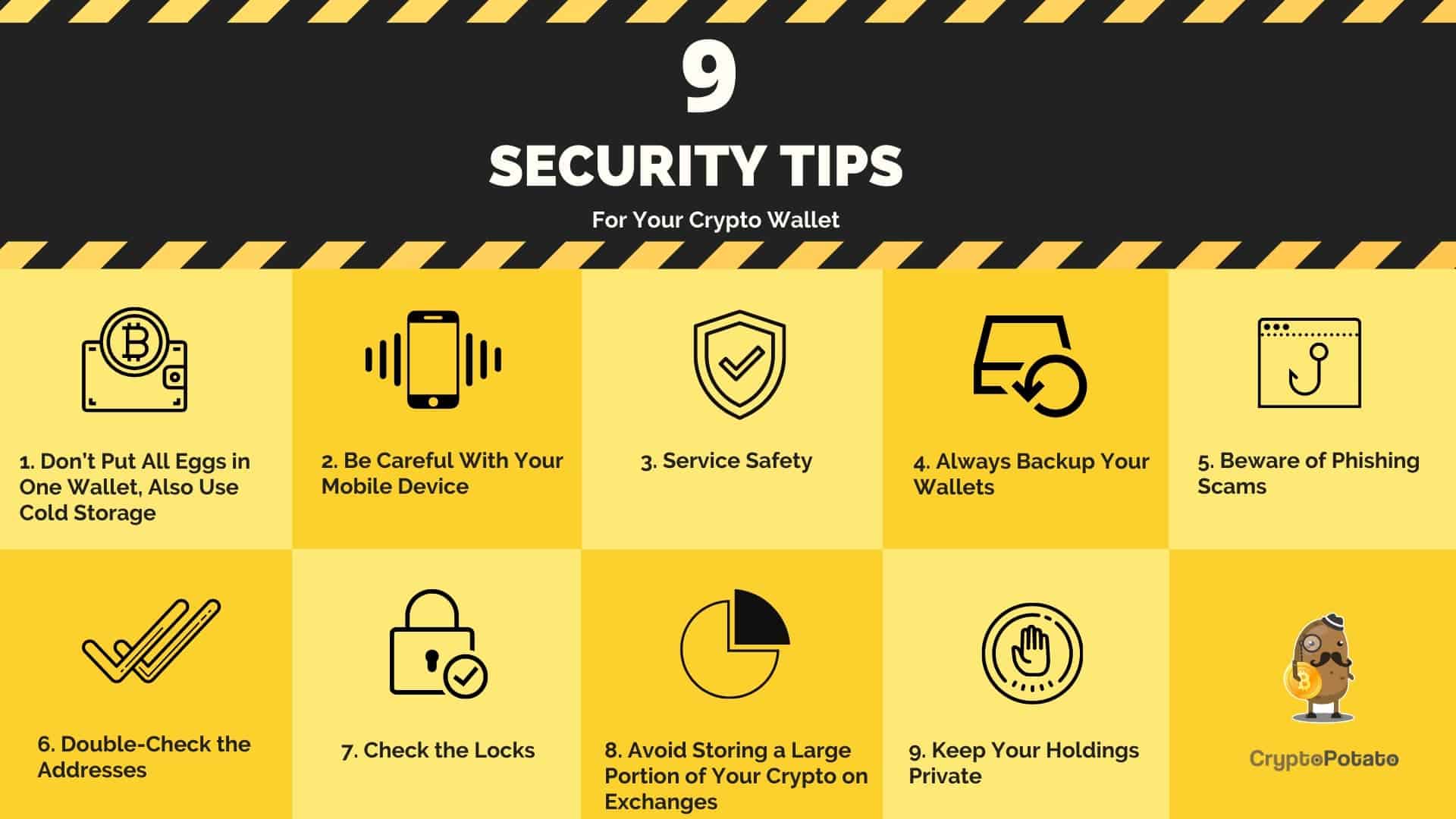
In the world of virtual currencies, managing your cryptocurrency securely is of utmost importance. One of the ways to store and access your digital assets is through hot wallets. Hot wallets are online wallets that are connected to the internet and are accessible through a website or an app.
Public and private keys are crucial components of hot wallets. A public key acts as an address to which you can receive your virtual currencies, while a private key allows you to access and manage your digital assets. It is important to keep your private key secure and never share it with anyone.
When using a hot wallet, it is essential to choose a reputable and trusted provider. Make sure to research the wallet’s security measures and read reviews from other users. Look for strong encryption protocols and multi-factor authentication to ensure the safety of your funds.
One of the advantages of hot wallets is their convenience. You can easily access your funds from any device with an internet connection. This makes hot wallets suitable for daily transactions and frequent trading. However, it is important to exercise caution when using hot wallets for large sums of money and consider keeping the majority of your funds in cold storage for added security.
- What is a hot wallet?
- Key points about hot wallets:
- How Does a Hot Wallet Work
- Overview of hot wallets
- Key features of hot wallets
- How Do I Keep a Hot Wallet Secure
- Choose a reputable hot wallet
- Implement strong security measures
- Regularly update and backup your wallet
- Best Practices for Hot Wallet Management
- Monitor your wallet activity
- Use a separate device for wallet management
- Enable multi-factor authentication
- Hot Wallet vs Hardware Wallet
- Differences between hot wallets and hardware wallets
- Pros and Cons of Hot Wallets
- Pros:
- Cons:
- When to use a hot wallet
- Final thoughts on hot wallet security
- Frequently Asked Questions:
- How can I securely manage my cryptocurrency?
- What is a hot wallet?
- What are the risks of using a hot wallet?
- How can I choose a reputable hot wallet provider?
- What is two-factor authentication and why is it important for hot wallets?
- Can I use a hot wallet for long-term storage of my cryptocurrency?
- Video:
- Top 5 Mobile Crypto Wallets: Safest Options for 2023
What is a hot wallet?
A hot wallet is a virtual wallet that holds your cryptocurrency and is connected to the internet. Unlike cold wallets, which are offline and disconnected from the internet, hot wallets are online and accessible through an internet connection. They are commonly used for day-to-day transactions and are easily accessible from different devices.
A hot wallet typically stores your cryptocurrency in a digital ledger, known as a blockchain. This ledger contains a record of all transactions made with your cryptocurrency. When you want to make a transaction, you authorize it using your private key, which is stored securely within your hot wallet.
One advantage of hot wallets is their convenience. They often come in the form of software or online services, allowing you to access your cryptocurrency from anywhere, as long as you have an internet connection. You can easily send and receive funds, check your balance, and manage your crypto assets without any hassle.
Hot wallets also provide you with a public address, which acts as your unique identifier on the blockchain. This address allows you to receive funds from others, as they can send funds to your public address. You can think of it as your virtual bank account number.
However, it’s worth mentioning that hot wallets are more susceptible to hacking and other security risks compared to cold wallets. Since they are constantly connected to the internet, there is a higher chance of unauthorized access or potential vulnerabilities. It is important to choose a reputable and secure hot wallet provider and take necessary precautions, such as enabling two-factor authentication and regularly updating your software.
Key points about hot wallets:
- A hot wallet is a virtual wallet connected to the internet.
- It stores your cryptocurrency in a digital ledger.
- Your private key authorizes transactions made with your hot wallet.
- Hot wallets provide a public address for receiving funds.
- They offer convenience but are more susceptible to security risks.
How Does a Hot Wallet Work
A hot wallet is a type of cryptocurrency wallet that is connected to the internet. It allows users to easily access and manage their cryptocurrency holdings.
When setting up a hot wallet, the user is provided with a unique address. This address acts as a ledger, keeping track of the user’s cryptocurrency transactions. The address is a combination of letters and numbers and is used to send and receive funds.
In order to authorize transactions, hot wallets require the user to provide their private key. This private key is a unique code that is associated with the user’s address. It is important to keep this private key secure, as anyone with access to it can access the funds in the wallet.
Hot wallets are typically accessed through a website or a mobile application. Once the user logs in to their hot wallet, they can view their balance, send funds to other addresses, and receive funds from others.
One key aspect of hot wallets is that they are public. This means that anyone can view the transaction history for a particular address. While the user’s identity is not directly linked to the address, it is important to be mindful of the privacy implications when using a hot wallet.
In summary, hot wallets are connected to the internet and allow users to easily manage their cryptocurrency holdings. They use a unique address to keep track of transactions and require a private key for authorization. Hot wallets are accessed through a website or mobile application and are public, meaning anyone can view the transaction history associated with a particular address.
Overview of hot wallets

Hot wallets are digital wallets that are connected to the internet and designed to store and manage your cryptocurrency. Unlike cold wallets, which are offline and offer a higher level of security, hot wallets are more convenient and easily accessible from anywhere as long as you have an internet connection.
Hot wallets can come in different forms, such as software wallets or online wallet services. Software wallets are applications that you can download and install on your computer or mobile device, while online wallet services are provided by websites that allow you to create an account and access your virtual wallet through their platform.
When using a hot wallet, you usually create an account with a wallet provider or download an application. This account or application generates a public key and a private key. The public key acts as your wallet address and allows other users to send you cryptocurrency. The private key is what you need to authorize transactions and access your funds.
Hot wallets store your private keys on an internet-connected device, whether it’s your computer or a server of the online wallet service. This means that there is always a risk of hacking or unauthorized access. It’s important to choose a reputable wallet provider and take necessary security measures, such as using strong passwords and enabling two-factor authentication.
While hot wallets offer convenience and easy access to your cryptocurrency, it’s important to remember that they are more vulnerable to security risks compared to cold wallets. Therefore, it’s recommended to only store small amounts of cryptocurrency in hot wallets for everyday use, while keeping the majority of your funds in cold storage for long-term security.
Key features of hot wallets
Hot wallets are digital wallets that are connected to the internet and are commonly used for convenience and quick access to cryptocurrencies. Here are some key features of hot wallets:
- Accessibility: Hot wallets allow users to easily access their cryptocurrency anytime and anywhere as long as they have an internet connection. They provide a user-friendly interface, making it convenient to manage and use cryptocurrencies.
- Public Ledger: Hot wallets are connected to the public ledger, also known as the blockchain. This allows users to view their transaction history and check the balance of their cryptocurrencies in real-time.
- Authorization: Hot wallets require users to authorize transactions by providing a private key or password. This adds an extra layer of security and ensures that only the authorized user can send or receive cryptocurrencies from the wallet.
- Address Generation: Hot wallets generate unique addresses for each transaction. These addresses are used to receive cryptocurrencies from other users or exchanges. Users can provide their wallet address to others to receive funds.
- Connected to Websites and Services: Hot wallets are often connected to cryptocurrency exchanges, enabling users to easily trade, buy, and sell cryptocurrencies from within the wallet interface. They can also be connected to other services or decentralized applications (DApps) for various purposes.
In conclusion, hot wallets offer accessibility, real-time transaction visibility, authorization, address generation, and connections to websites and services. However, it’s important to note that hot wallets are more susceptible to security threats compared to cold wallets, which are offline storage options for cryptocurrencies.
How Do I Keep a Hot Wallet Secure

A hot wallet is a type of cryptocurrency wallet that is connected to the internet and accessible through a website or software application. While hot wallets offer convenience and ease of use, they also pose a higher risk of security breaches compared to cold wallets.
Here are some best practices to keep your hot wallet secure:
- Choose a reputable wallet provider: When selecting a hot wallet, research and choose a trusted and well-established wallet provider. Look for wallets that have a good reputation and positive user reviews.
- Enable two-factor authentication (2FA): Two-factor authentication adds an extra layer of security to your hot wallet. Enable 2FA by linking your wallet to an authenticator app or using SMS authentication.
- Use a strong and unique password: Create a strong password that includes a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using common passwords or using the same password for multiple accounts.
- Regularly update your wallet software: Keep your hot wallet software up to date to benefit from the latest security patches and improvements. Wallet providers often release updates to address vulnerabilities and bugs.
- Secure your device: Ensure that the device you use for accessing your hot wallet is secure. Use reputable antivirus software, regularly update your operating system, and avoid downloading or installing suspicious programs.
- Keep your private keys offline: Hot wallets typically store your private keys on their servers. However, for added security, consider using a hardware wallet or a software wallet that allows you to export and securely store your private keys offline.
- Regularly check for suspicious activity: Monitor your wallet activity regularly and be vigilant for any unauthorized transactions or access attempts. If you notice any suspicious activity, immediately contact your wallet provider and take appropriate action.
- Be cautious when using public Wi-Fi: Avoid accessing your hot wallet or performing any transactions while connected to public Wi-Fi networks. Public Wi-Fi networks are often unsecured, making it easier for hackers to intercept your data.
- Double-check website addresses: Before entering your wallet credentials or performing any actions, verify that you are on the correct website. Scammers may create fake websites that look similar to the official wallet provider’s site to steal your information.
- Keep your public address private: While hot wallets rely on public addresses for receiving funds, it’s important to keep your public address private. Sharing your public address with others can increase the risk of targeted attacks or scams.
By following these security measures, you can help protect your hot wallet and reduce the risk of potential security breaches or unauthorized access to your cryptocurrency funds.
Choose a reputable hot wallet
When it comes to managing your cryptocurrency, one of the most important decisions you will make is choosing a reputable hot wallet. A hot wallet is a digital wallet that is connected to the internet, making it accessible and convenient for transactions.
It is crucial to choose a reputable hot wallet because you will be authorizing them to hold and manage your virtual currency. This means they will have access to your funds and private keys, so you want to ensure that they have a track record of security and trust.
Here are some key factors to consider when choosing a reputable hot wallet:
- Security: Look for a wallet that offers advanced security features such as two-factor authentication, encryption, and multisig support. These features can greatly enhance the protection of your funds.
- Reputation: Do some research and read reviews about the wallet provider. Look for wallets that have been in the market for a while and have a good track record of security and customer satisfaction.
- Transparency: Choose a wallet provider that is transparent about their security practices and has a clear privacy policy. They should also provide regular updates and communicate openly with their users.
- User-friendly interface: A good hot wallet should have an intuitive and user-friendly interface that makes it easy for you to navigate and manage your funds.
- Supported cryptocurrencies: Make sure that the hot wallet you choose supports the cryptocurrencies you plan to store and manage. Some wallets may only support a limited number of currencies.
Additionally, it is important to note that reputable hot wallets will never ask for your private keys or password. They should provide you with a public address for receiving funds, but not require you to disclose your private keys.
By choosing a reputable hot wallet, you can have peace of mind knowing that your funds are stored securely and managed by a trusted provider.
Implement strong security measures

When it comes to managing your cryptocurrency, implementing strong security measures is essential to protect your digital assets from unauthorized access. Here are some important steps to follow:
- Keep your private keys private: Your private keys are the main access point to your funds. Keep them secure and never share them with anyone. Make sure to store them in a safe and encrypted location.
- Use a strong and unique password: Create a password that is difficult to guess and avoid using common phrases or personal information. It is also important to use a different password for each of your accounts.
- Enable two-factor authentication: Two-factor authentication adds an extra layer of security to your accounts. By requiring both your password and a unique code generated by an app or sent to your mobile device, it significantly reduces the risks of unauthorized access.
- Regularly update your software: Keep your operating system and wallet software up to date with the latest security patches. This helps to address vulnerabilities and protect against potential attacks.
- Be cautious of public Wi-Fi networks: Public Wi-Fi networks are often insecure and can be easily compromised. Avoid accessing your wallet or conducting any sensitive transactions while connected to public Wi-Fi.
- Utilize hardware wallets: Hardware wallets provide an extra layer of security by storing your private keys offline in a secure device. They are not connected to the internet, making it extremely difficult for hackers to gain access to your funds.
- Verify the website: When accessing your wallet online, make sure to double-check the website’s URL and ensure that it is legitimate. Phishing attacks can lead you to fake websites that aim to steal your credentials.
- Regularly backup your wallets: It is crucial to regularly backup your wallets and store the backup files in secure locations. This ensures that you can recover your funds in case of any hardware failures or accidental loss.
- Stay informed about security best practices: Keep yourself updated with the latest security trends and best practices in the cryptocurrency industry. Following cryptocurrency news and staying informed about potential threats will help you stay one step ahead of hackers.
By implementing these strong security measures, you can significantly enhance the security of your hot wallets and protect your cryptocurrency from unauthorized access.
Regularly update and backup your wallet
When it comes to managing your cryptocurrency in a hot wallet, it’s crucial to keep your wallet software up to date. Regularly updating your wallet is important because it ensures you have the latest security enhancements and bug fixes, reducing the risk of potential vulnerabilities.
In addition to updating your wallet, it’s essential to create regular backups of your wallet data. These backups serve as a safety net in case something goes wrong with your wallet, such as accidental deletion or hardware failure.
To backup your wallet, you’ll need to locate the wallet file or the 12 or 24-word passphrase, depending on the wallet you’re using. It’s recommended to store these backups in multiple secure locations, such as external hard drives, encrypted USB drives, or cloud storage with strong security measures.
One popular method for storing wallet backups is using a hardware wallet, such as Ledger or Trezor. These wallets securely store your private keys offline, reducing the risk of online threats. They often have a backup and recovery option that allows you to restore your wallet in case of loss or damage.
| Practice | Description |
|---|---|
| Regularly update your wallet software | Update your wallet software to have the latest security enhancements and bug fixes. |
| Create regular backups | Backup your wallet data in multiple secure locations to protect against accidental loss or hardware failure. |
| Consider using a hardware wallet | Use a hardware wallet to securely store your private keys offline and have a backup and recovery option. |
| Store backups securely | Keep your wallet backups in encrypted storage options, such as external hard drives, encrypted USB drives, or cloud storage with strong security measures. |
By regularly updating and backing up your wallet, you can ensure that your connected hot wallets have the latest security measures and that your cryptocurrency holdings are protected in case of any unforeseen events or breaches.
Best Practices for Hot Wallet Management
Hot wallets are digital wallets that are connected to the internet and used for managing and transacting with cryptocurrencies. They are convenient for quick access and easy transactions, but they also pose certain security risks. Here are some best practices for managing hot wallets securely:
- Choose reputable wallets: When selecting a hot wallet, ensure that you choose a reputable and trustworthy provider. Look for wallets that have a good track record of security and have been audited by third-party security firms.
- Enable two-factor authentication: Two-factor authentication adds an extra layer of security to your hot wallet. Enable this feature and use it whenever possible to protect your wallet from unauthorized access.
- Use strong and unique passwords: Set a strong and unique password for your hot wallet. Avoid using common passwords and consider using a password manager to generate and store complex passwords.
- Regularly update your wallet software: Keep your hot wallet software up to date with the latest security patches and updates. Regularly check for updates and apply them as soon as they are available.
- Regularly back up your wallet: Create regular backups of your hot wallet to protect against data loss. Store the backup in a secure location, preferably offline or in a secure cloud storage service.
- Be cautious with public Wi-Fi: Avoid accessing your hot wallet or entering sensitive information on public Wi-Fi networks. Public Wi-Fi networks are often insecure and can be easily compromised by hackers.
- Double-check the recipient’s address: When making cryptocurrency transactions, double-check the recipient’s address before confirming the transaction. Cryptocurrency transactions are irreversible, so any mistakes can lead to permanent loss of funds.
- Only visit official wallet websites: When accessing your hot wallet, make sure you are visiting the official website of the wallet provider. Beware of phishing attempts and avoid clicking on suspicious links or downloading software from untrusted sources.
- Monitor your wallet activity: Regularly review your hot wallet activity and look for any suspicious or unauthorized transactions. Report any suspicious activity immediately to your wallet provider.
By following these best practices, you can help secure your hot wallet and protect your cryptocurrencies from unauthorized access or theft.
Monitor your wallet activity
As a cryptocurrency holder, it’s crucial to regularly monitor your wallet activity to stay informed about any incoming or outgoing transactions. By keeping track of your wallet activity, you can quickly identify any unauthorized access or suspicious behavior.
Here are some steps you can take to monitor your wallet activity:
- Keep your public address private: It’s essential to keep your wallet’s public address private and only share it with trusted individuals or entities. Your public address is like your virtual identity in the cryptocurrency world, and anyone who knows it can track your transactions.
- Regularly check your connected websites: If you have connected your wallet to any websites or services, it’s important to regularly review those connections. Ensure that the websites or services you have authorized to access your wallet are reputable and trustworthy. Unauthorized or suspicious connections should be immediately removed.
- Set up wallet alerts: Most reputable wallets offer the option to set up alerts for specific activities. You can customize these alerts to notify you when a transaction above a certain amount occurs, or when there is any login activity on your wallet. These alerts can help you stay vigilant and quickly respond to any suspicious activity.
- Monitor transaction history: Regularly review the transaction history of your wallet. Ensure that all transactions were authorized by you and match your expectations. Any unauthorized or suspicious transactions should be reported to your wallet provider immediately.
- Enable two-factor authentication (2FA): Two-factor authentication adds an extra layer of security to your wallet. By enabling 2FA, you will receive an additional code on your mobile device or email whenever you attempt to log in or perform a transaction. This helps prevent unauthorized access even if someone knows your wallet’s password.
By following these practices and staying vigilant, you can better protect your cryptocurrency holdings and ensure the security of your wallet.
Use a separate device for wallet management

When it comes to managing your virtual currency wallet, it’s important to keep security in mind. One way to enhance the security of your wallet is to use a separate device for wallet management. By having a dedicated device, you can reduce the risk of your wallet being compromised.
Here are some steps you can take to implement this strategy:
- Choose a secure device: Select a device that is known for its security features, such as a hardware wallet. Hardware wallets like Ledger offer an extra layer of protection by keeping your private keys offline.
- Keep the device offline: When managing your wallet, it’s best to keep the device disconnected from the internet. This prevents any potential malware or hackers from gaining access to your wallet.
- Connect to trusted websites: When connecting your device to the internet for wallet management purposes, ensure that you only access trusted websites. Be cautious of phishing websites that may try to steal your wallet information.
- Verify the address: Before making any transactions, double-check the wallet address to ensure you are sending your funds to the correct recipient. Mistakenly sending funds to the wrong address can result in permanent loss.
By following these guidelines and utilizing a separate device for wallet management, you can significantly enhance the security of your cryptocurrency holdings. Remember, keeping your private keys secure is crucial for protecting your funds.
Enable multi-factor authentication

Multi-factor authentication (MFA) provides an additional layer of security for your cryptocurrency wallets. By enabling MFA, you add an extra step to the login process, requiring the use of a second form of verification before accessing your wallet.
There are several types of MFA methods available, including:
- Text message verification codes
- Email verification codes
- Time-based one-time passwords (TOTP)
- Hardware tokens
When setting up MFA for your hot wallets, it is important to choose a method that is convenient for you but also provides a high level of security.
To enable MFA, follow these general steps:
- Go to the website or platform where your hot wallet is connected.
- Locate the security or account settings section.
- Look for the option to enable MFA.
- Choose the desired MFA method.
- Follow the instructions to set up MFA, which may include verifying your phone number or email address.
- Once MFA is enabled, you will be prompted to enter the verification code each time you log in to your wallet.
By enabling MFA, you add an extra layer of security to your hot wallet, making it more difficult for unauthorized individuals to access your funds. It adds an additional step of verification, ensuring that only you, as the authorized user, can access and authorize transactions from your wallet.
Hot Wallet vs Hardware Wallet
When it comes to managing your cryptocurrency, there are two main types of wallets to consider: hot wallets and hardware wallets. Each has its own advantages and disadvantages, and it’s important to understand the differences between them before deciding which one is right for you.
A hot wallet is a type of cryptocurrency wallet that is connected to the internet. It can be accessed through a website or mobile app, allowing users to manage their cryptocurrency holdings and perform transactions. Hot wallets are convenient and easy to use, but they are also more vulnerable to hacks and online attacks.
A hardware wallet, on the other hand, is a physical device that securely stores a user’s cryptocurrency private keys offline. These wallets are typically in the form of a USB stick or a small device, like a ledger. Hardware wallets are considered to be the most secure way to store cryptocurrency because they are not connected to the internet, making it nearly impossible for hackers to gain access to the private keys.
One of the main differences between hot wallets and hardware wallets is the level of security they provide. Hot wallets are more susceptible to hacks and online attacks because they are connected to the internet. On the other hand, hardware wallets offer an additional layer of security by keeping the private keys offline. This makes them ideal for those who want to securely store their cryptocurrency for a long period of time.
Another difference between the two types of wallets is the ease of use. Hot wallets are generally easier to set up and use, as they can be accessed through a website or mobile app. Hardware wallets, on the other hand, require a bit more technical knowledge to set up and operate. However, once set up, they offer a more secure and reliable way to manage cryptocurrency.
Hot wallets are also known to have a public address associated with them. This means that anyone can see the transactions made from a hot wallet, as the address is visible on the blockchain. In contrast, hardware wallets use private keys that are not visible to the public. This provides an added layer of privacy and security.
In summary, hot wallets are convenient and easy to use, but they come with a higher risk of being hacked. Hardware wallets are more secure, but they require more technical knowledge to set up and operate. Ultimately, the choice between the two depends on your individual needs and preferences.
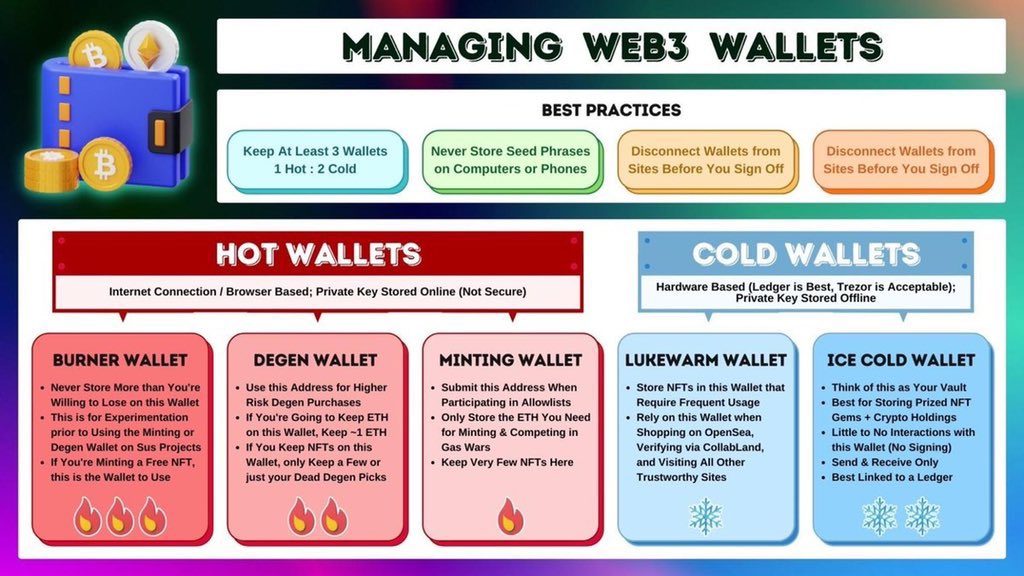
Differences between hot wallets and hardware wallets
Hot wallets and hardware wallets are two different types of cryptocurrency wallets that offer different levels of security and accessibility.
Hot wallets:
- Hot wallets are connected to the internet and are accessible from any device with an internet connection.
- They generate and store cryptocurrency addresses, which can be used to send and receive funds.
- Hot wallets are typically provided by cryptocurrency exchanges or online wallet services.
- They are convenient for frequent trading or accessing funds on the go.
- However, as hot wallets are connected to the internet, they are more vulnerable to hacking attacks and malware.
Hardware wallets:
- Hardware wallets, on the other hand, are physical devices that store cryptocurrency private keys offline.
- They require a physical connection to a device, such as a computer or smartphone, in order to authorize transactions.
- Hardware wallets use secure elements to protect private keys, making them more secure against hacking attempts.
- They often come with a built-in display for confirming transaction details and have buttons for user input.
- Hardware wallets are not connected to the internet when generating or signing transactions, providing an added layer of security.
While hot wallets are more convenient for accessing funds and making quick transactions, hardware wallets offer a higher level of security for long-term storage of cryptocurrency.
It is important to note that both hot wallets and hardware wallets rely on the same public ledger, known as the blockchain, to validate and record transactions. However, the difference lies in how the private keys are managed and protected.
Pros and Cons of Hot Wallets
A hot wallet is a type of cryptocurrency wallet that is connected to the internet. These wallets are often provided as a service by cryptocurrency exchange websites or other third-party providers. While they offer convenience and accessibility, hot wallets also come with their own set of pros and cons.
Pros:
- Convenience: Hot wallets are easily accessible from any device with an internet connection. Users can manage their cryptocurrency funds and make transactions from anywhere at any time.
- User-friendly interfaces: Most hot wallets have intuitive interfaces that make it easy for beginners to use and navigate.
- Speed: Transactions made with hot wallets are typically faster compared to other types of wallets.
- Support for multiple cryptocurrencies: Many hot wallets support a wide range of cryptocurrencies, allowing users to manage multiple virtual assets in one place.
Cons:
- Security risks: Hot wallets are more susceptible to hacking and cyber attacks compared to offline wallets. Since they are connected to the internet, they are inherently more vulnerable.
- Dependency on third parties: Users of hot wallets are reliant on the security measures implemented by the third-party provider. If the provider’s website or infrastructure is compromised, users’ funds may be at risk.
- Public addresses: Hot wallets often generate and use public addresses, which are visible on the blockchain. This lack of privacy can be a concern for some users.
- Less control over private keys: In hot wallets, the private keys are typically stored on the provider’s server. This means that users have less control over their own keys, increasing the risk of theft or loss if the provider is compromised.
Overall, hot wallets offer convenience and accessibility, but users should be aware of the inherent security risks and make sure to take necessary precautions to protect their funds.
When to use a hot wallet
A hot wallet is a type of connected cryptocurrency wallet that allows users to authorize and manage their virtual assets on various platforms. They are typically web-based wallets that are accessible through a website.
Hot wallets are commonly used for day-to-day transactions and are great for storing small amounts of cryptocurrency that you plan to spend or trade in the near future. Here are some situations in which you might want to use a hot wallet:
- Convenience: Hot wallets provide easy access to your cryptocurrency at any time and from anywhere with an internet connection. They are user-friendly and can be accessed from any device with a web browser.
- Speed: Hot wallets allow for quick and immediate transactions. This is especially useful when you need to make fast payments or take advantage of time-sensitive trading opportunities.
- Small transactions: If you frequently make small transactions, such as buying goods or services online, a hot wallet is a convenient option. It is more practical to store a small amount of cryptocurrency in an easily accessible hot wallet.
However, it’s important to note that hot wallets are connected to the internet and can be vulnerable to hacking attempts. If you are storing a large amount of cryptocurrency or want a higher level of security, you may want to consider using a cold wallet, such as a hardware wallet or a paper wallet.
Final thoughts on hot wallet security

In conclusion, hot wallets are a convenient option for managing your cryptocurrency on a daily basis. However, it’s important to prioritize security when using these virtual wallets.
When choosing a hot wallet, make sure to select a reputable provider with a secure website. Look for wallets that utilize multisig technology, which requires multiple signatures to authorize transactions. This provides an extra layer of security.
It’s also crucial to always double-check the address you are sending your cryptocurrency to. Scammers may try to trick you into sending funds to their own address instead. Verify the destination address every time you initiate a transaction.
Remember that hot wallets store your private keys online, making them more susceptible to hacking attempts. Keep your device and wallet software up to date to protect against any vulnerabilities that may arise.
Finally, it’s critical to keep an eye on the public ledger, or blockchain, to monitor the activity and balances of your hot wallet. By regularly reviewing your transaction history, you can quickly identify any unauthorized or suspicious activity.
By following these best practices and remaining vigilant, you can help ensure the security of your hot wallet and the funds it contains.
Frequently Asked Questions:
How can I securely manage my cryptocurrency?
There are several ways to securely manage your cryptocurrency. One option is to use a hot wallet, which is a digital wallet connected to the internet. Hot wallets are convenient for daily transactions but may be susceptible to hacking or theft. To enhance security, it’s important to choose a reputable hot wallet provider, enable two-factor authentication, and regularly update the wallet software.
What is a hot wallet?
A hot wallet is a type of digital wallet that is connected to the internet. It allows users to easily access and manage their cryptocurrency for daily transactions. Hot wallets are often provided by cryptocurrency exchanges or online wallet services. However, since they are connected to the internet, there is a higher risk of hacking or theft compared to cold wallets.
What are the risks of using a hot wallet?
Using a hot wallet comes with certain risks. Since hot wallets are connected to the internet, they may be vulnerable to hacking or theft. If a hacker gains access to your hot wallet, they could potentially steal your cryptocurrency. Additionally, if the hot wallet provider experiences a security breach, your funds may be at risk. It’s important to take precautions such as choosing a reputable provider and implementing additional security measures to mitigate these risks.
How can I choose a reputable hot wallet provider?
When choosing a hot wallet provider, it’s important to consider factors such as the provider’s reputation, security features, customer reviews, and user interface. You should look for a provider that has a strong track record of security and a transparent approach to customer support. It’s also advisable to choose a provider that offers two-factor authentication and regularly updates their wallet software to protect against emerging threats.
What is two-factor authentication and why is it important for hot wallets?
Two-factor authentication is an additional layer of security that requires users to provide two types of identification before accessing their hot wallet. This typically involves entering a password and then providing a second form of identification, such as a verification code sent to a mobile device. Two-factor authentication is important for hot wallets because it adds an extra barrier of protection against unauthorized access. Even if a hacker manages to obtain your password, they would still need the second form of identification to gain access to your wallet.
Can I use a hot wallet for long-term storage of my cryptocurrency?
While hot wallets are convenient for daily transactions, they are not typically recommended for long-term storage of cryptocurrency. Since hot wallets are connected to the internet, they are more susceptible to hacking or theft compared to cold wallets, which are offline. If you plan on holding a large amount of cryptocurrency for an extended period, it’s generally safer to use a cold wallet for storage and only keep a small portion of your funds in a hot wallet for immediate spending.
Video:
Top 5 Mobile Crypto Wallets: Safest Options for 2023








