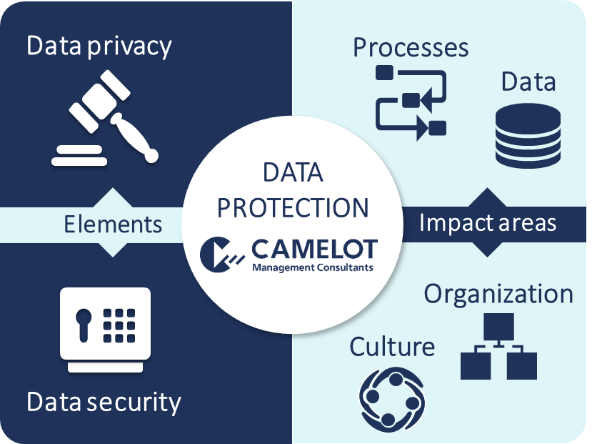
In today’s digital age, data security and privacy have become increasingly important. With the growing reliance on technology and the increasing threats of cyber attacks, organizations and individuals must take steps to protect their sensitive information.
One crucial aspect of ensuring data protection and privacy is conducting regular audits. Audits involve a thorough examination of a system or process to assess its security measures and identify any potential vulnerabilities. Audits provide valuable insights into areas that need improvement and help organizations stay one step ahead of potential threats.
It is essential to understand what data needs to be protected and why. Different types of data, such as personal information, financial records, or intellectual property, may require different levels of security. Organizations must prioritize their efforts based on the sensitivity of the data they handle.
Additionally, individuals and organizations must keep pace with the ever-evolving landscape of cybersecurity threats. Regularly updating security software and systems, implementing strong passwords, and educating employees about best practices can go a long way in protecting data. It is important not to underestimate the potential risks and to stay proactive in safeguarding sensitive information.
- Tangem Wallet: The Ultimate Solution
- Features and Benefits
- How Tangem Wallet Works
- Mobile App for Tangem Wallet
- Convenient and User-friendly Interface
- Securely Send and Receive Payments
- Managing Multiple Digital Assets
- Choose Your Payment Method
- Tangem Wallet Integration with Various Payment Systems
- Securely Linking your Bank Account
- Using Cryptocurrencies for Hassle-free Transactions
- Frequently Asked Questions:
- What does data protection and privacy mean?
- Why is data protection important?
- What are some common methods or practices used for data protection?
- How can individuals protect their own data and privacy?
- Video:
- Data Security vs Data Privacy
- Online Privacy & Security 101: How To Actually Protect Yourself?
Tangem Wallet: The Ultimate Solution

Tangem Wallet is a revolutionary solution that addresses the growing concerns around data protection and privacy. In a world where digital threats are constantly evolving, Tangem Wallet provides a secure and reliable platform for storing and managing personal information.
One of the key features of Tangem Wallet is that it ceases to be an attractive target for hackers. By using cutting-edge encryption technology, Tangem Wallet ensures that personal data is stored in a secure and tamper-proof manner. This means that even if the device is lost or stolen, the user’s sensitive information remains protected.
But what sets Tangem Wallet apart from other solutions is its focus on transparency and accountability. Tangem Wallet undergoes regular third-party audits to ensure that the highest standards of security are met. These audits examine the encryption algorithms used, as well as the hardware and software components of the wallet.
In addition to its robust security features, Tangem Wallet also offers a user-friendly interface that makes it easy for individuals to manage their personal information. With just a few clicks, users can securely store and access their data, such as passwords, credit card information, and social security numbers.
Tangem Wallet also goes beyond just protecting personal data. It offers a range of additional features, such as two-factor authentication and biometric verification, to further enhance security. These measures ensure that only authorized individuals can access the wallet and the information stored within it.
Overall, Tangem Wallet is the ultimate solution for individuals who value their privacy and want to ensure that their personal information is protected. With its secure encryption technology, regular third-party audits, and user-friendly interface, Tangem Wallet provides a comprehensive and reliable platform for data protection and privacy.
Features and Benefits
When it comes to ensuring data protection and privacy, there are several key features and benefits that should not be ignored. By implementing security measures that address these features, organizations can significantly reduce the risk of breaches and unauthorized access to sensitive information.
- Encryption: One of the most important features of a secure data protection system is encryption. Encryption ensures that data is encoded using complex algorithms, making it extremely difficult for unauthorized individuals to access or decipher the information.
- Access control: Another essential feature is the implementation of strict access control measures. This includes defining user roles and permissions, as well as incorporating multi-factor authentication and strong password policies. By limiting access to sensitive data, organizations can minimize the risk of unauthorized access.
- Auditing and monitoring: An effective data protection system should include auditing and monitoring capabilities. This allows organizations to track and monitor user activities, detect any irregularities or suspicious behavior, and take immediate action if necessary.
- Regular updates and patches: To remain secure, it is crucial to keep software and systems up to date with the latest updates and patches. This ensures that any vulnerabilities or weaknesses are addressed, minimizing the risk of exploitation.
- Data backup and recovery: In the event of a data breach or loss, having a robust data backup and recovery process in place is essential. Regularly backing up data and testing the recovery process can help organizations quickly restore data and minimize downtime.
- Compliance with regulations: Organizations must ensure that they comply with relevant data protection and privacy regulations. Failure to comply can result in severe consequences, including legal and financial penalties.
By incorporating these features into their data protection systems, organizations can benefit from enhanced security, reduced risk of data breaches, and improved compliance with regulations. It is crucial not to underestimate the importance of securing sensitive data, as the consequences of a breach can be far-reaching and long-lasting.
| Features | Benefits |
|---|---|
| Encryption | Protects data from unauthorized access |
| Access control | Restricts access to sensitive information |
| Auditing and monitoring | Provides visibility into user activities |
| Regular updates and patches | Addresses vulnerabilities and strengthens security |
| Data backup and recovery | Ensures data can be restored in case of loss or breach |
| Compliance with regulations | Avoids legal and financial penalties |
How Tangem Wallet Works
Tangem Wallet is a secure and convenient solution for storing and managing digital assets like cryptocurrencies. It employs innovative technology to ensure the privacy and protection of user data.
One of the key features of Tangem Wallet is that it operates offline. Unlike traditional online wallets that are susceptible to hacking and data breaches, Tangem Wallet functions without an internet connection. This means that the risk of unauthorized access to your digital assets ceases to exist.
To use Tangem Wallet, you simply need to tap your Tangem card to a smartphone or NFC-enabled device. The card contains a built-in chip that securely stores your private keys and performs cryptographic operations. This eliminates the need to enter sensitive information on your phone, further enhancing the security of your digital assets.
In addition to its offline capabilities, Tangem Wallet also provides a unique way to ensure the integrity of your digital assets. Each Tangem card is equipped with a special security chip that records every transaction made with the card. This allows users to easily verify the history and authenticity of their digital assets, providing an extra layer of protection against fraud and tampering.
Tangem Wallet is designed with user privacy in mind. Unlike some other wallet providers, Tangem Wallet does not collect or store any personal data. Your private keys are securely stored on the Tangem card and never leave the card, ensuring that only you have access to your digital assets.
When it comes to security and privacy, Tangem Wallet sets a high standard. Its offline functionality, secure chip technology, and commitment to user privacy make it a reliable and convenient choice for storing and managing your digital assets.
Mobile App for Tangem Wallet
Tangem is a company that specializes in manufacturing secure hardware wallets for storing and managing cryptocurrencies. Their wallets are designed to be easy to use, secure, and reliable. One of the ways Tangem ensures the security and privacy of their users’ data is through the development of a mobile app specifically for their wallets.
The mobile app serves as an interface between the user and the Tangem wallet, allowing them to access and manage their cryptocurrencies with ease. The app undergoes regular audits to ensure that it meets the highest security standards and that it remains resilient against potential threats.
One of the key features of the Tangem mobile app is its ability to securely store private keys. Private keys are essential for cryptocurrency transactions, as they are used to sign and authorize transactions on the blockchain. Tangem utilizes advanced encryption techniques to protect these keys, ensuring that they are never exposed to potential attackers. In addition, the app employs several layers of security measures, such as biometric authentication and PIN codes, to further enhance the protection of users’ private keys.
Another important aspect of the Tangem mobile app is its focus on privacy. Tangem understands the importance of keeping users’ personal information confidential, and they don’t collect any unnecessary data that could compromise their privacy. The app only requires basic user information for setup and does not store any personal data on the device or on their servers.
The security and privacy measures implemented by Tangem don’t cease with the mobile app alone. Tangem wallets themselves are built with advanced security features, such as secure element chips and tamper-evident packaging, which offer additional layers of protection against physical attacks and unauthorized access.
In summary, the Tangem mobile app plays a crucial role in ensuring the security and privacy of users’ cryptocurrency holdings. Through regular audits and the implementation of strong security measures, Tangem provides a trustworthy and reliable solution for managing and protecting cryptocurrencies on their hardware wallets.
Convenient and User-friendly Interface
When it comes to ensuring data protection and privacy, it is essential to have a convenient and user-friendly interface. A well-designed interface helps users easily navigate through different features and settings, ensuring that they can efficiently manage their data and privacy preferences.
One of the key factors in a user-friendly interface is simplicity. Users shouldn’t have to struggle to find the necessary options or settings to protect their data. The interface should be intuitive and clearly organized, with easily accessible menus and controls.
Another aspect of a convenient interface is customization. Different users have different needs and preferences when it comes to data protection and privacy. A good interface allows users to customize their settings and preferences according to their specific requirements, without overwhelming them with unnecessary options.
Furthermore, an audit feature can contribute to the convenience of the interface. Users should have access to a log that shows them what actions have been taken on their data, such as who accessed it and when. This helps users understand the level of security their data enjoys and can be particularly useful in detecting any unauthorized access or misuse.
It is also important to provide clear and concise explanations of the different features and settings available. Users should be able to understand what each option does and how it affects their data protection and privacy. Clear instructions and tooltips can help users make informed decisions and avoid any unintended consequences.
In summary, a convenient and user-friendly interface is crucial when it comes to ensuring data protection and privacy. It should be simple, customizable, and provide clear explanations. Additionally, having an audit feature can further enhance the convenience of the interface, allowing users to monitor and track their data’s security.
Securely Send and Receive Payments
In today’s digital age, online payments have become a crucial part of everyday life. Whether it’s paying for goods and services or sending money to friends and family, the convenience of online payments is unmatched. However, with convenience comes the need for security and protection of sensitive financial information.
When it comes to sending and receiving payments securely, it is essential to use trusted and reputable payment platforms. These platforms have robust security measures in place to protect your financial data from unauthorized access and ensure the privacy of your transactions.
One of the key security measures that these platforms employ is encryption. Encryption converts your financial data, such as credit card numbers and banking details, into an unreadable format. This ensures that even if intercepted, the data cannot be deciphered without the proper decryption key. By using encryption, your sensitive information remains secure throughout the payment process.
Additionally, reputable payment platforms often implement multi-factor authentication. This means that besides entering your password, you may also be required to provide additional authentication factors, such as a unique code sent to your mobile device or a fingerprint scan. This extra layer of security ensures that only authorized individuals can access your account and authorize payments.
Furthermore, these platforms undergo regular audits to ensure compliance with industry standards and regulations. Audits, performed by independent third-party companies, assess the security measures in place and identify any vulnerabilities or weaknesses. By conducting audits, payment platforms can identify and address any potential security risks before they can be exploited.
As a user, it is also important to take certain precautions to enhance the security of your online payments. Ensure that your devices are protected with up-to-date antivirus software and operating system patches. Be cautious while entering your financial information and avoid doing so on public Wi-Fi networks or unsecured websites. Regularly monitor your payment accounts for any suspicious or unauthorized activity.
In conclusion, securely sending and receiving payments online is paramount to protect your financial information and maintain your privacy. By using trusted payment platforms that employ encryption, multi-factor authentication, and undergo regular audits, you can rest assured that your transactions are secure. Additionally, practicing good cybersecurity habits and being vigilant while using online payment services will further enhance your protection.
Managing Multiple Digital Assets
When it comes to managing multiple digital assets, it is important to have an efficient system in place that ensures their security and privacy. Digital assets can range from personal files, such as documents and photos, to important business data and sensitive customer information.
One of the first things to consider is conducting a thorough audit of your digital assets. This includes identifying what types of data you have, where it is stored, and who has access to it. By knowing what you have, you can better implement security measures to protect it.
For example, it is crucial to have strong passwords in place for all your digital assets. Using a combination of uppercase and lowercase letters, numbers, and special characters can make it harder for unauthorized individuals to gain access.
Another important aspect to consider is encryption. Encryption is the process of converting data into a code to prevent unauthorized access. By encrypting your digital assets, even if someone gains access to them, they won’t be able to read or use the information without the encryption key.
What you don’t want to do is rely solely on technology to manage your digital assets. While technology can be an effective tool, it is important to also have proper protocols and procedures in place.
- Regularly backing up your digital assets is essential. This ensures that even if something were to happen to the original files, you will still have a copy.
- Limiting access to your digital assets to only those who need it can also enhance security. By granting permissions and using role-based access control, you can ensure that only authorized individuals can access sensitive information.
- Training employees on safe practices when it comes to managing digital assets is also crucial. This includes educating them on the importance of using strong passwords, recognizing phishing attempts, and being cautious when sharing files.
In conclusion, managing multiple digital assets requires a proactive approach to ensure their security and privacy. By conducting regular audits, implementing strong passwords and encryption, and having proper protocols and procedures in place, you can protect your valuable data from unauthorized access.
Choose Your Payment Method

When it comes to online shopping and transactions, choosing the right payment method is crucial. With the increasing threat of data breaches and online fraud, it is important to ensure that your personal and financial information is secure.
Here are some popular payment methods to consider:
-
Credit Card: One of the most common payment methods used online is a credit card. It offers convenience and ease of use, allowing you to make purchases instantly. However, it is important to be cautious and only provide your credit card information on secure websites that have proper encryption measures in place.
-
Debit Card: Similar to a credit card, a debit card allows you to make online purchases using funds from your bank account. However, using a debit card online can put your bank account at risk if unauthorized transactions occur. Make sure to regularly monitor your bank statements and report any suspicious activity to your bank immediately.
-
PayPal: PayPal is a popular online payment system that allows you to securely link your bank account or credit card to make purchases. It adds an extra layer of security by not directly sharing your financial information with the merchant. PayPal also has buyer protection policies in place, offering refunds in case of unauthorized transactions or disputes.
-
Mobile Payment Apps: With the rise of smartphones, mobile payment apps have gained popularity. These apps, such as Apple Pay and Google Wallet, allow you to make purchases by linking your credit card or bank account to your mobile device. They use encryption and tokenization technology to protect your payment information.
-
Cryptocurrencies: For those looking for an alternative payment method, cryptocurrencies like Bitcoin and Ethereum offer a decentralized and secure option. However, it’s important to note that the value of cryptocurrencies can be volatile, and transactions are irreversible. Additionally, using cryptocurrencies requires technical knowledge and caution to avoid scams and phishing attempts.
Regardless of the payment method you choose, it is essential to be vigilant and practice good security measures. Regularly review your financial statements, enable two-factor authentication whenever possible, and ensure that the websites you are transacting on are secure and use SSL encryption. Performing regular audits of your accounts and transactions can help you detect any suspicious activity and take necessary action to protect your data.
Tangem Wallet Integration with Various Payment Systems

In today’s digital age, the use of mobile wallets has become increasingly popular. These wallets allow users to store their payment information securely on their mobile device for convenient and quick payments. One such mobile wallet is the Tangem Wallet, which offers a unique and secure solution for storing and using payment information.
Unlike traditional mobile wallets, the Tangem Wallet ceases the need for internet connectivity during transactions. It uses NFC technology to transfer payment information securely between the mobile device and the payment terminal. This eliminates the risk of hacking and unauthorized access to sensitive data.
What sets the Tangem Wallet apart is its integration capabilities with various payment systems. It can be easily linked to existing payment systems, such as credit cards, bank accounts, and online payment platforms. This allows users to make payments with their Tangem Wallets at any merchant or online store that accepts these payment methods.
Furthermore, the Tangem Wallet offers enhanced security features to protect user data. It uses encryption algorithms to safeguard payment information, ensuring that it is securely stored and transferred. Additionally, the wallet undergoes regular security audits to identify and address any vulnerabilities, providing users with peace of mind when using the wallet for their transactions.
To make the user experience even more seamless, the Tangem Wallet provides a user-friendly interface. It is designed to be intuitive and easy to navigate, ensuring that users can access their payment information and make transactions quickly and efficiently.
In conclusion, the integration of the Tangem Wallet with various payment systems offers users a secure and convenient solution for storing and using their payment information. With its offline transaction capabilities, robust security features, and compatibility with different payment methods, the Tangem Wallet is a strong contender in the mobile wallet market.
Securely Linking your Bank Account
In today’s digital world, it has become increasingly convenient to link your bank account to various online platforms and services. From paying bills to managing your finances, the ability to securely link your bank account allows for a seamless user experience. However, it is important to understand the risks and take necessary precautions to ensure the protection of your sensitive financial information.
What are the risks?
- Unauthorized access: When you link your bank account to any platform, there is always a risk of unauthorized access. Hackers can potentially gain access to your bank account and misuse your funds or personal information.
- Fraudulent activities: If your bank account is linked to an insecure platform, cybercriminals may use your financial information for fraudulent activities, such as making unauthorized purchases.
- Data breaches: Platforms that store your bank account information may become victims of data breaches, resulting in the exposure of your sensitive financial data.
- Identity theft: If a cybercriminal gains access to your bank account, they may also be able to steal your identity by using your personal information for fraudulent purposes.
What should you do?
- Choose reputable platforms: When linking your bank account, opt for well-established and reputable platforms. Research the platform’s security measures and privacy policies to ensure they meet industry standards.
- Enable two-factor authentication (2FA): Use platforms that offer two-factor authentication as an additional layer of security. This can help protect your bank account even if your login credentials are compromised.
- Regularly monitor your bank account: Keep an eye on your bank account activity and immediately report any suspicious transactions or activities to your bank. Regularly reviewing your statements can help detect unauthorized access.
- Keep your devices secure: Ensure that your computer, smartphone, or any device you use to access your bank account is protected with strong passwords, up-to-date antivirus software, and secure browsing practices.
- Audit linked accounts: Periodically review the platforms and services that have access to your bank account. Remove any unnecessary or unused links to minimize the risk of unauthorized access.
Conclusion
While linking your bank account to online platforms can provide convenience, it’s essential to prioritize security and take the necessary steps to protect your sensitive financial information. Being cautious about the platforms you choose, enabling two-factor authentication, and regularly monitoring your bank account can help safeguard against unauthorized access and fraudulent activities.
Using Cryptocurrencies for Hassle-free Transactions

In today’s digital age, where technology is rapidly advancing, the use of cryptocurrencies has become increasingly popular for hassle-free transactions. Cryptocurrencies, such as Bitcoin, offer a secure and decentralized way to transfer funds and make purchases online.
One of the main advantages of using cryptocurrencies is the ability to make transactions quickly and easily. Traditional banking systems often involve lengthy processes, such as verifying identities and conducting audits, which can cause delays and additional expenses. With cryptocurrencies, transactions can be completed almost instantly, eliminating the need for time-consuming processes.
Another benefit of using cryptocurrencies is the high level of security they provide. When making a payment with a cryptocurrency, the transaction is encrypted and recorded in a public ledger called the blockchain. This ensures that the transaction is secure and cannot be tampered with. Additionally, cryptocurrencies utilize advanced encryption techniques to protect user information, offering a high level of privacy.
Furthermore, using cryptocurrencies for transactions allows individuals to maintain control over their funds. Unlike traditional banking systems, where a third party acts as an intermediary, cryptocurrencies enable users to have full ownership and control of their funds. This eliminates the risk of funds being frozen or seized.
Moreover, cryptocurrencies offer a global payment solution that transcends borders. Traditional payment methods often involve currency conversion fees and other charges when making international transactions. With cryptocurrencies, these fees and charges are significantly reduced or even eliminated, making it a cost-effective solution for international payments.
It is important to note, however, that the value of cryptocurrencies can be volatile, which means their worth can fluctuate rapidly. This can result in potential gains or losses for individuals using cryptocurrencies for transactions. Therefore, it is essential for users to stay informed and educated about the market to make informed decisions.
| Advantages of Using Cryptocurrencies for Transactions: |
|---|
|
In conclusion, cryptocurrencies offer a hassle-free and secure way to make transactions in today’s digital world. With benefits such as quick transactions, high security, and global payment capabilities, cryptocurrencies are becoming an increasingly popular choice. However, it is important to stay informed about the market and understand the potential risks and benefits associated with using cryptocurrencies for transactions.
Frequently Asked Questions:
What does data protection and privacy mean?
Data protection and privacy refer to the measures and practices taken to ensure that personal and sensitive information is secure and not accessible by unauthorized individuals.
Why is data protection important?
Data protection is important because it helps protect sensitive information, such as personal details, financial data, and medical records, from falling into the wrong hands. It helps ensure privacy and prevent identity theft, fraud, and other forms of cybercrime.
What are some common methods or practices used for data protection?
Some common methods or practices used for data protection include strong password policies, encryption, regular data backups, using secure networks and firewalls, implementing access controls, and regularly updating software and systems.
How can individuals protect their own data and privacy?
Individuals can protect their own data and privacy by using strong and unique passwords, being cautious about sharing personal information online, avoiding suspicious websites and downloads, regularly updating their devices and software, and using reputable security software.
Video:
Data Security vs Data Privacy
Online Privacy & Security 101: How To Actually Protect Yourself?